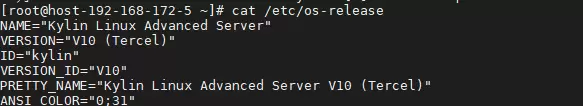
cat /etc/os-release uname -r
 常见情况参考:
常见情况参考:ssh -V
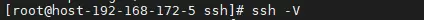 若输出显示为 OpenSSH 8.2p1,则系统很可能为基于 CentOS 8 的 Kylin V10 服务器版本。
若输出显示为 OpenSSH 8.2p1,则系统很可能为基于 CentOS 8 的 Kylin V10 服务器版本。
警告:此方法可能导致 SSH 服务无法启动或登录失败!必须确保具备本地控制台、IPMI、VNC 或串口等备用访问方式。
提示:由于 yum 包管理器最高仅支持升级至 OpenSSH_8.2p1,因此需通过源码手动升级。
sudo yum groupinstall "Development Tools" -y
sudo yum install zlib-devel openssl-devel pam-devel tcp_wrappers-devel -y
cd /opt
wget https://cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-9.9p1.tar.gz
tar -zxvf openssh-9.9p1.tar.gz
cd openssh-9.9p1
./configure \
--prefix=/usr \
--sysconfdir=/etc/ssh \
--with-pam \
--with-ssl-engine \
--with-zlib \
--without-gssapi # 关键!禁用 GSSAPI 以消除 sha1 相关算法
make && sudo make install
sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
sudo /usr/sbin/sshd -t
sudo systemctl restart sshd
ssh -V
sshd -T | grep gssapikexalgorithms # 正常情况下应无输出
--without-gssapiyum/apt[root@host-192-168-172-5 ~]# cat /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.103 2018/04/09 20:41:22 tj Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# This sshd was compiled with PATH=/usr/local/bin:/usr/bin:/usr/local/sbin:/usr/sbin
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
Port 22222
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# Logging
#SyslogFacility AUTH
SyslogFacility AUTH
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#PubkeyAuthentication yes
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedPrincipalsFile none
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
PermitEmptyPasswords no
PasswordAuthentication yes
# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes
# GSSAPI options
#GSSAPIAuthentication yes
#GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
#GSSAPIEnablek5users no
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in kylin and may cause several
# problems.
UsePAM yes
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
PrintMotd no
#PrintLastLog yes
#TCPKeepAlive yes
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#UseDNS no
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
Banner none
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS
# override default of no subsystems
Subsystem sftp /usr/libexec/openssh/sftp-server -l INFO -f AUTH
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
#CheckUserSplash yes
# To modify the system-wide ssh configuration, create a *.conf file under
# /etc/ssh/sshd_config.d/ which will be automatically included below
#Include /etc/ssh/sshd_config.d/*.conf
Protocol 2
LogLevel VERBOSE
PubkeyAuthentication yes
#RSAAuthentication yes
IgnoreRhosts yes
#RhostsRSAAuthentication no
HostbasedAuthentication no
PermitEmptyPasswords no
PermitUserEnvironment no
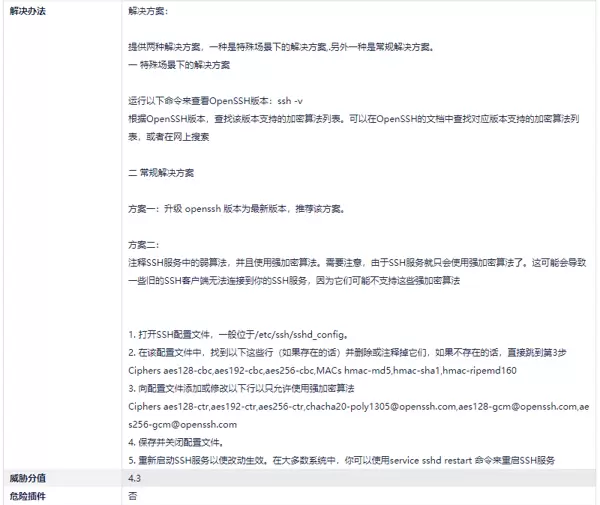
#Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com
ClientAliveCountMax 0
Banner /etc/issue.net
#MACs hmac-sha2-512,hmac-sha2-512-etm@openssh.com,hmac-sha2-256,hmac-sha2-256-etm@openssh.com,hmac-sha1,hmac-sha1-etm@openssh.com
StrictModes yes
AllowTcpForwarding no
AllowAgentForwarding no
GatewayPorts no
PermitTunnel no
#KexAlgorithms curve25519-sha256,curve25519-sha256@libssh.org,diffie-hellman-group14-sha1,diffie-hellman-group-exchange-sha1,diffie-hellman-group-exchange-sha256
# 强制使用安全加密套件(覆盖默认值)
Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr
MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com
KexAlgorithms curve25519-sha256,curve25519-sha256@libssh.org,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512
ssh -V
# 应输出:OpenSSH_9.9p1 ...
sshd -T | grep -i gssapi
若无任何输出,则表示相关算法已成功移除。
sudo update-crypto-policies --set LEGACY # 或临时设为 DEFAULT 并排除冲突项重启服务后测试是否恢复。 方案 B:修改 systemd 服务文件,绕过 crypto-policies 限制
sudo systemctl edit sshd插入以下内容:
[Service] Environment=OPENSSL_ENABLE_SHA1_SIGNATURES=1保存并重载配置:
sudo systemctl daemon-reexec sudo systemctl restart sshd
sshd -T | grep -i gssapikexalgorithms预期结果:无输出,表示该算法已被彻底移除。
gssapikexalgorithms检查 SSH 配置中是否仅包含 gssapiauthentication no(或其他禁用设置),且未配置 gssapikexalgorithms。
验证弱加密算法是否已清除,执行以下命令:
sshd -T | grep -E 'ciphers|macs|kexalgorithms'确保输出结果中不包含 arcfour、cbc、sha1 或 3des 等不安全算法。
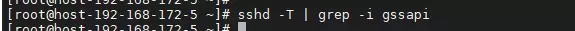
服务无法正常启动。
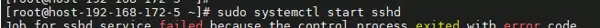
[root@host-192-168-172-5 ~]# sudo journalctl -u sshd -n 20 --no-pager
-- Logs begin at Sun 2025-05-18 14:11:09 CST, end at Tue 2025-11-25 15:49:04 CST. --
11月 25 15:47:23 host-192-168-172-5 sshd[3536277]: command-line: line 0: Bad configuration option: GSSAPIKexAlgorithms
11月 25 15:47:23 host-192-168-172-5 systemd[1]: sshd.service: Main process exited, code=exited, status=1/FAILURE
11月 25 15:47:23 host-192-168-172-5 systemd[1]: sshd.service: Failed with result 'exit-code'.
11月 25 15:47:23 host-192-168-172-5 systemd[1]: Failed to start OpenSSH server daemon.
11月 25 15:48:05 host-192-168-172-5 systemd[1]: sshd.service: Service RestartSec=42s expired, scheduling restart.
11月 25 15:48:05 host-192-168-172-5 systemd[1]: sshd.service: Scheduled restart job, restart counter is at 26.
11月 25 15:48:05 host-192-168-172-5 systemd[1]: Stopped OpenSSH server daemon.
11月 25 15:48:05 host-192-168-172-5 systemd[1]: Starting OpenSSH server daemon...
11月 25 15:48:06 host-192-168-172-5 sshd[3536600]: command-line: line 0: Bad configuration option: GSSAPIKexAlgorithms
11月 25 15:48:06 host-192-168-172-5 systemd[1]: sshd.service: Main process exited, code=exited, status=1/FAILURE
11月 25 15:48:06 host-192-168-172-5 systemd[1]: sshd.service: Failed with result 'exit-code'.
11月 25 15:48:06 host-192-168-172-5 systemd[1]: Failed to start OpenSSH server daemon.
11月 25 15:48:48 host-192-168-172-5 systemd[1]: sshd.service: Service RestartSec=42s expired, scheduling restart.
11月 25 15:48:48 host-192-168-172-5 systemd[1]: sshd.service: Scheduled restart job, restart counter is at 27.
11月 25 15:48:48 host-192-168-172-5 systemd[1]: Stopped OpenSSH server daemon.
11月 25 15:48:48 host-192-168-172-5 systemd[1]: Starting OpenSSH server daemon...
11月 25 15:48:48 host-192-168-172-5 sshd[3536910]: command-line: line 0: Bad configuration option: GSSAPIKexAlgorithms
11月 25 15:48:48 host-192-168-172-5 systemd[1]: sshd.service: Main process exited, code=exited, status=1/FAILURE
11月 25 15:48:48 host-192-168-172-5 systemd[1]: sshd.service: Failed with result 'exit-code'.
11月 25 15:48:48 host-192-168-172-5 systemd[1]: Failed to start OpenSSH server daemon.关键错误信息如下:
sshd[3536277]: command-line: line 0: Bad configuration option: GSSAPIKexAlgorithms在通过 systemd 启动时,系统尝试通过命令行传入特定参数:
GSSAPIKexAlgorithms然而,当前安装的 OpenSSH 版本为 9.9p1,该版本在编译过程中已禁用 GSSAPI 支持:
--without-gssapi由于二进制程序无法识别与 GSSAPI 相关的启动选项,导致解析失败并直接退出(exit 1)。
sshd查看系统的 systemd 服务配置文件:
EnvironmentFile=-/etc/crypto-policies/back-ends/opensshserver.config
ExecStart=/usr/sbin/sshd -D $OPTIONS $CRYPTO_POLICY $PERMITROOTLOGIN其中引用的环境变量:
$CRYPTO_POLICY来源于以下配置文件:
/etc/crypto-policies/back-ends/opensshserver.config该文件内容可能包含类似如下设置:
CRYPTO_POLICY="-o GSSAPIKexAlgorithms=gss-group14-sha1-,gss-gex-sha1-"而当前使用的 OpenSSH 是手动编译且明确关闭了 GSSAPI 功能,因此:
sshd当你手动运行 sshd 命令时,并未加载 systemd 的环境配置:
$CRYPTO_POLICY因此不会传入导致问题的 CRYPTO_POLICY 参数,从而避免了错误。
sshd -tsshd -D -e此方法最为彻底和安全:
sudo rm -f /etc/crypto-policies/back-ends/opensshserver.config或创建一个空文件以防止服务报错:
sudo touch /etc/crypto-policies/back-ends/opensshserver.configsudo systemctl daemon-reloadsudo systemctl start sshd此操作将使
$CRYPTO_POLICY为空值,不再传递任何可能导致冲突的启动参数。
-o通过复制并编辑服务文件,强制忽略 CRYPTO_POLICY:
sudo cp /usr/lib/systemd/system/sshd.service /etc/systemd/system/sshd.service使用 sed 删除变量引用:
sudo sed -i 's/ \$CRYPTO_POLICY//' /etc/systemd/system/sshd.service或直接手动编辑替换以下行:
[Service]
...
ExecStart=/usr/sbin/sshd -D $OPTIONS $PERMITROOTLOGIN
...完成后执行:
sudo systemctl daemon-reloadsudo systemctl start sshdExecStart检查配置文件是否仍包含问题参数:
cat /etc/crypto-policies/back-ends/opensshserver.config若输出类似:
CRYPTO_POLICY='-o GSSAPIKexAlgorithms=...,gss-gex-sha1-'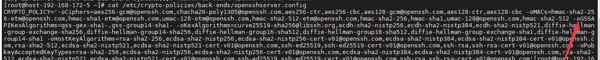
则可确认该配置正是引发故障的根本原因。
GSSAPIKexAlgorithmssudo pkill -f "sshd"sudo rm -f /etc/crypto-policies/back-ends/opensshserver.configsudo touch /etc/crypto-policies/back-ends/opensshserver.configsudo systemctl daemon-reloadsudo systemctl start sshdsystemctl status sshd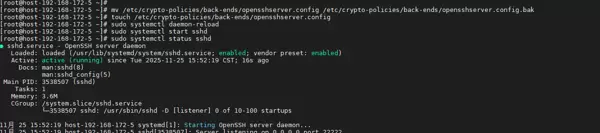
systemctl status sshd→ active (running)
sshd -T | grep gssapi→ 不再出现无效参数错误
gssapikexalgorithms安全扫描工具将不再因弱算法或错误配置报告高危风险。
OpenSSH 9.0 及以上版本默认隐藏未启用的算法,但前提是不能传入非法或无效的命令行选项。
Kylin 或 CentOS 中的 crypto-policies 机制是为系统自带的 OpenSSH 设计的,手动编译的版本需主动规避其影响。
只需执行方案 A,即可彻底解决问题。
完成之后,你的 OpenSSH 9.9p1 将以完全干净、安全且符合规范的状态稳定运行。
最终建议
针对不同环境下的服务器,推荐采取以下应对措施:
测试或非关键服务器
建议手动编译并部署 OpenSSH 9.9 及以上版本以满足安全要求。
--without-gssapi生产服务器(允许停机)
推荐将系统升级至 Kylin V10 SP3、openEuler 22.03 或 Rocky Linux 9 等支持更高 OpenSSH 版本的发行版。
生产服务器(不允许停机)
可暂维持现有配置,同时提交《误报说明》进行备案处理;
或通过部署 SSH 跳板机的方式实现安全合规与业务连续性的平衡。
 扫码加好友,拉您进群
扫码加好友,拉您进群



 收藏
收藏